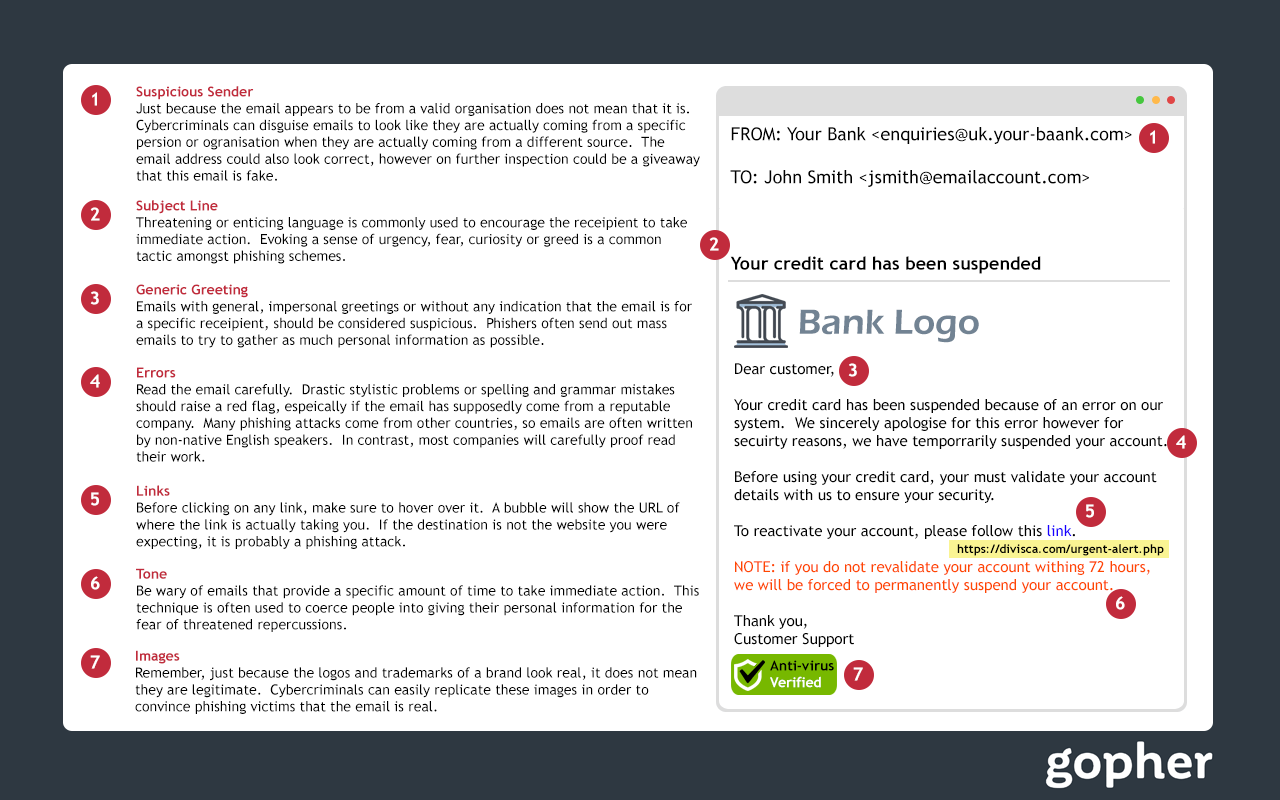
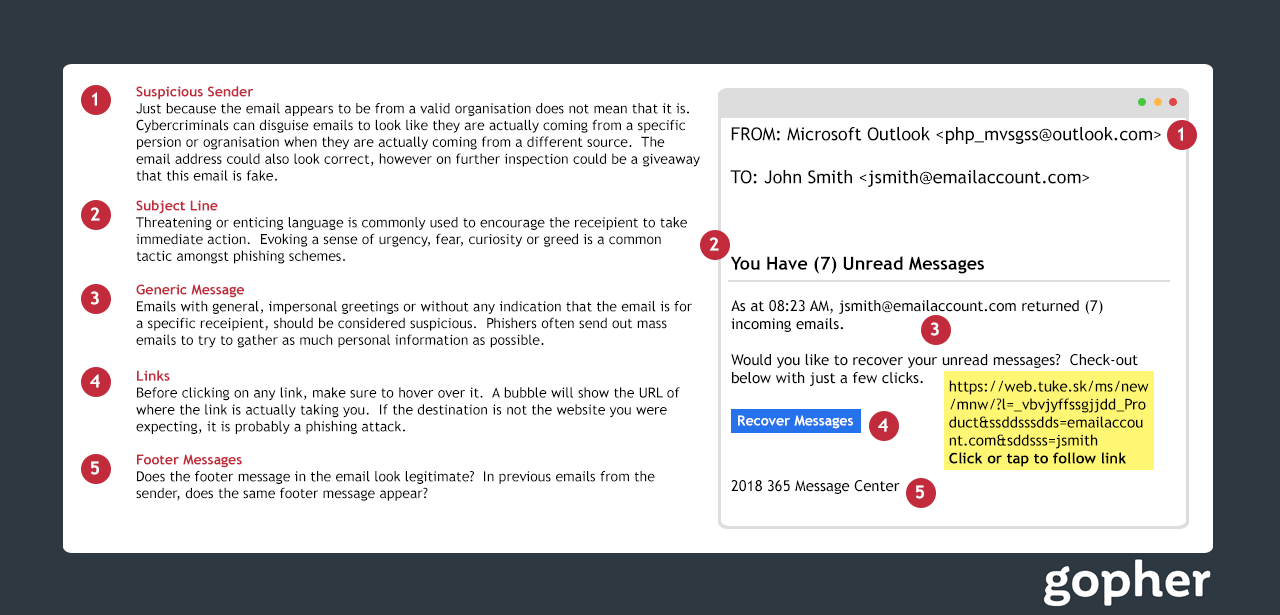
Like a fisherman hoping for his next big catch, cyber criminals attempt to lure users with legitimate looking mass emails in what’s known as a phishing attack. The goal is to fool users into handing over login credentials, downloading malware or to get you to visit a malicious website.
This simple and stunningly effective attack is more often prevalent than not.
According to PhishMe’s Enterprise Phishing Resiliency and Defence Report, phishing attempts have grown 65% in the last year.
The fact is most organisations don’t have adequate email security measurements in place to protect against Office 365 attacks and even those that do, cyber criminals are finding new ways to bypass security measures and trick users into handing over their information.
It’s so easy to trick a user
It’s really easy for a cyber criminal to pull off a phishing attack. They design counterfeit emails and websites to look like they come from a trusted brand – perhaps a retailer, technology company or even a bank. Busy users will recognise the brand but fail to notice slight differences that give away the imposter. In their defence, those differences could can be as small as a minor difference in the URL.
So how do you detect a phishing email?
There are some good ones that are not so obvious and then there are some bad ones which should be really obvious. We’ll go through both below:
What happens when you click the link?
Once a user clicks the link in a phishing email, they will be taken to a web page where the sky is the limit. Usually, however, there is a web form where attackers might request:
- Access credentials to corporate resources like your ERP system or cloud-based applications.
- Access credentials to the users’ personal accounts (which users often reuse across multiple accounts including your corporate accounts).
- Sensitive financial information, either the users’ own or one belonging to the company.
- Proprietary company information.
Whatever information the attacker successfully collects can then be used to conduct additional attacks. For example, attackers might use access credentials to break into and move around the corporate network or sell the sensitive and confidential data they’ve obtained.
Spear-phishing attacks
Phishing attacks are pretty bad, but believe it or not, it actually gets worse. While phishing attacks are conducted against a large group of users, spear-phishing attacks target specific individuals. Spear-phishing attacks are specifically written to appeal to an individual using relevant details and sometimes posing as a trusted colleague, a friend, or pretty much anyone you could imagine someone would trust.
These attacks have higher success rates than generic phishing attacks and present a much bigger problem for companies as they often target critical employees like executives and IT professionals.
The social engineering behind a spear-phishing attack is easy, inexpensive and stunningly effective.
It’s easy for an attacker to bypass email security measures
Signature based solutions such as Microsoft’s built in EOP solution identify patterns in the email. This is an effective approach for blocking known threats that are circulating the internet. Once someone falls victim to a phishing attack and the email or attachment is identified as malicious, a signature file is created and used to protect other users.
Cyber attackers simply won’t call it quits once a signature is created for their attack. Instead they continually alter the code so that the malicious software no longer matches the known signature in an attempt to avoid detection.
Most spear-phishing attacks don’t actually contain malware or malicious links. Attackers will simply pose as colleague or partner asking for information. E.g. “Hey, I’m just having lunch with a client, the CEO just texted me for the financial pro-formas, can you send them to me ASAP?”. Because emails like this look valid to most filters, they will never match a signature file.
In order to defend against phishing attacks, you need predictive email security that compliments Microsoft’s EOP. Next generation security solutions leverage artificial intelligence, predictive analytic’s and machine learning to stop unknown threats.
If you would like more information on how we can help you stop threats, send us an email through the contact page.